Safe Words App
YOUR BRAIN IS THE PASSWORD VAULT

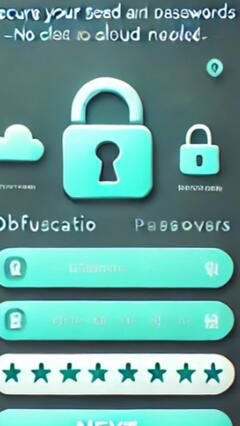
Safewords is a new way to secure your most sensitive information like seed phrases, passwords, PINs. Using only your memory and a short passcode, Lifeprint transforms your unique life experiences into a private, zero-knowledge security system that only you can unlock.Safewords is designed for privacy, security, and accessibility—helping you take control of your data in a way that is both intuitive and resilient. No data is stored. No information is shared. Everything is offline.📌 No Cloud, No Servers, No Storage – Lifeprint operates entirely on your device without saving your data.
📌 Memorize Less, Secure More – Your own life events become your key, eliminating the need to remember complex passwords.
📌 Works Offline – Whether you're traveling or in an emergency, Lifeprint functions without an internet connection.
📌 Accessible & Easy to Use – Built with simplicity and usability in mind, Lifeprint is ideal for everyone, including the elderly.🔒 Your secrets remain yours alone. Experience security that works the way your mind does.
Offline Redundancy & Accessibility
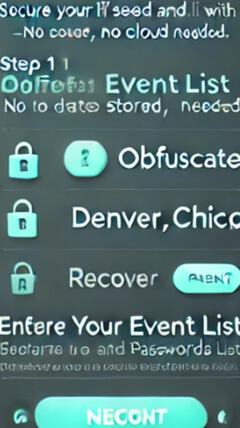
One of the biggest challenges in digital security is dependence on online services. What happens if you lose access to your accounts when traveling? Or in an emergency where you don’t have your password manager?Instead of memorizing random numbers, passwords, and security questions, why not use the deep memories already stored in your brain?We all have lists inside our minds—things we will never forget:The cities we’ve lived in (in order)The pets we’ve had (first to last)The addresses we’ve called homeThe teachers we rememberThe cars we've ownedThis personal sequence of events—your Lifeprint—is the foundation of your security system.How It Works:Choose a memorable list from your life experiences.Pair it with a short PIN (like a year or a simple number sequence).Use Lifeprint to transform passwords & seed phrases into something only you can reconstruct.Recover instantly—just re-enter your life events and PIN, and Lifeprint reconstructs the original information.Why This Works:✔ Impossible to brute force – No one else can guess how you ordered your life events.
✔ Simple yet secure – No need to remember complex passphrases.
✔ Works offline & anywhere – No dependency on apps or services.
Eu mi bibendum
✔ No reliance on cloud backups.
✔ Works without Wi-Fi, mobile data, or servers.
✔ Perfect for disaster preparedness, travel, and offline security.
Semper feugiat
Lifeprint is built for everyone, including those who struggle with memorization or complex passwords. For the elderly, caregivers, and those with cognitive challenges, Lifeprint offers an easier way to secure information without frustration.
Suscipit tellus
With Lifeprint, you don't need an internet connection, a cloud account, or a physical device. Your most important credentials are protected by the one thing always with you—your own mind.
Auctor eu augue
Lifeprints are more than just another security tool, it’s a new way to protect your data using knowledge that only you possess. Whether you're managing cryptocurrency, keeping track of work passwords or ensuring your digital security Lifeprints provide a seamless way to store secrets without storing anything at all.
Crypto Wallets
Disguise your seed phrase by transforming it into a unique set of words that only you can decipher—ensuring that even if someone finds your list, they cannot access your funds.
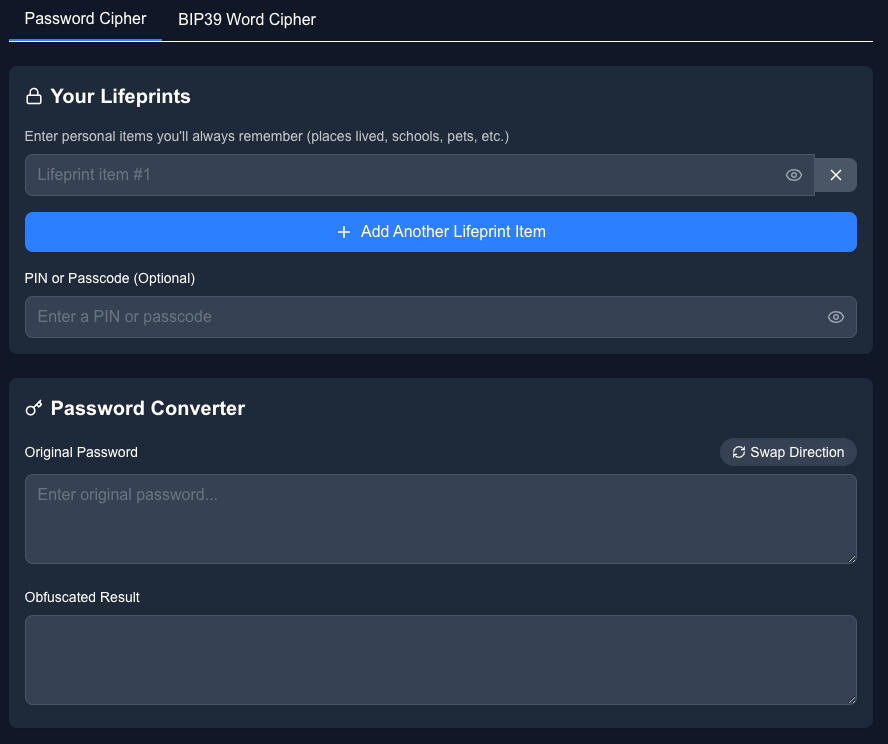
Passwords & More
Managing multiple work passwords can be challenging, and resetting credentials is a hassle. With Safewords - your brain + passcode = your master key.
Sed et ultrices
One of the biggest challenges in digital security is dependence on online services. What happens if you lose access to your accounts when traveling? Or in an emergency where you don’t have your password manager?
Standard
FREE
Elit duis tristique sollicitudin nibh sit congue mauris rhoncus aenean vel elit scelerisque mauris
Sed pulvinar etiam non quam lacus suspendisse
Magna lobortis mattis aliquam faucibus purus in massa tempor adipiscing feugiat
Premium
$9.99
Advertisements removed from app
Class aptent taciti sociosqu ad litora torquent nostra per magna inceptos himenaeos
Etiam tristique libero eu nibh porttitor etiam amet fermentum nullam venenatis lorem ipsum
Malesuada magna
Lorem ipsum at risus viverra adipiscing at in tellus integer feugiat. Vulputate odio ut enim blandit volutpat maecenas volutpat.
© Untitled. All rights reserved.
Technical Overview
Leverage your life lists for a zero-trust cipher security system.
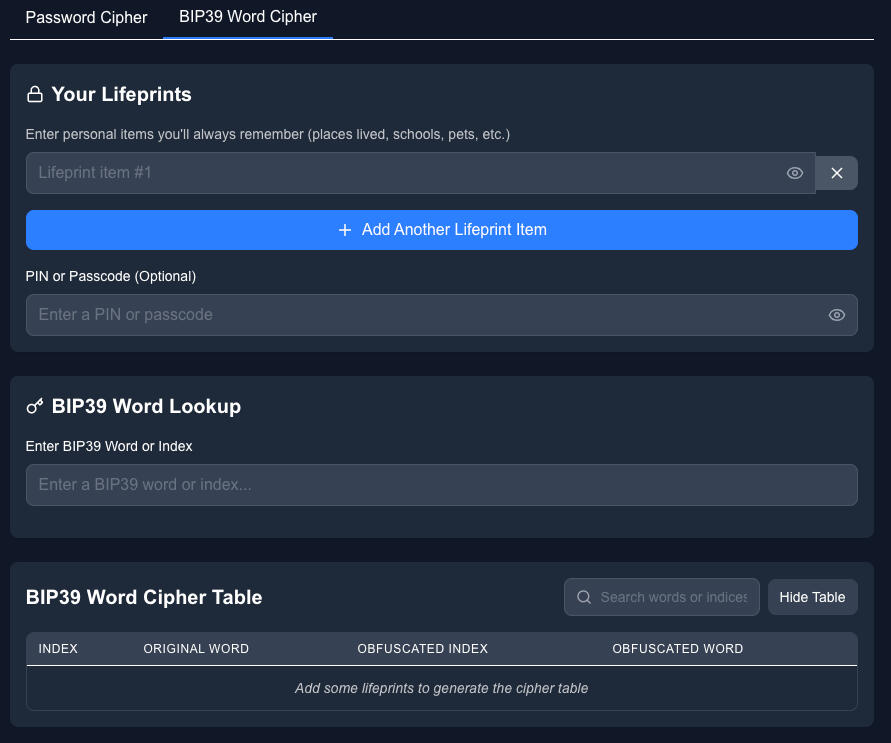
# Technical Documentation: Lifeprints - A Zero-Trust Cipher SystemOverviewLifeprints is a zero-trust cipher system that uses personally meaningful information as keys to generate deterministic transformations for sensitive data. Unlike traditional password managers or encryption tools that store keys or encrypted data, Lifeprints requires no persistent storage, operates completely offline, and relies solely on information already stored in the user's memory.This document explains the mathematical foundations and algorithmic procedures that make Lifeprints work.Core Concepts### 1. Memory-Based KeysLifeprints leverages the concept of "memory anchors" - information deeply embedded in a person's memory (childhood home, first pet, elementary school, etc.). These anchors serve as inputs to the system and replace traditional stored keys or passwords. The fundamental insight is that humans naturally retain certain autobiographical information with extremely high durability and recall accuracy, making these ideal for cryptographic seed material.### 2. Deterministic TransformationThe system creates bidirectional ciphers that transform:
- Passwords (character-level transformation)
- BIP39 seed phrases (word-level transformation)The transformations are fully deterministic - given the same lifeprint inputs, the system will always generate identical cipher mappings, allowing for reliable decoding without storing any mapping information.Mathematical FoundationString NormalizationInput strings (lifeprints and optional PIN) undergo normalization:The result is a single normalized string that serves as the basis for the cipher generation.Hash FunctionThe normalized string is processed using a 32-bit hash function similar to the djb2 algorithm:For a string S with length n:
1. Concatenation of all non-empty inputs
2. Conversion to lowercase
3. Removal of extraneous whitespace
1. Initialize hash h = 0
2. For each character c at position i (0 ≤ i < n):
- Update h = ((h << 5) - h) + charCode(c)
- Constrain h to 32 bits with bitwise AND: h = h & h
3. Take the absolute value of h as the final hashThis produces a deterministic numeric seed value that uniquely represents the combined lifeprint inputs.Seeded Pseudo-Random Number Generator (PRNG)The hash value seeds a linear congruential generator (LCG) with the following parameters:
- Multiplier: 9301
- Increment: 49297
- Modulus: 233280The PRNG function is defined as:
seed = (seed * 9301 + 49297) % 233280
random_value = seed / 233280 // Normalized to [0,1)
1. For i from n-1 down to 1:
- Generate j = floor(PRNG() * (i+1)) where 0 ≤ j ≤ i
- Swap A[i] and A[j]This algorithm runs in O(n) time and produces a permutation with all possible arrangements having equal probability when using a fair random number generator.Cipher GenerationPassword Cipher (ASCII Character Mapping)1. Create an array of 95 printable ASCII characters (code points 32-126)
2. Create an array of indices [0,1,2,...,94]
3. Apply the seeded Fisher-Yates shuffle to the indices array
4. Create a bidirectional mapping where:
- Forward mapping: originalchar[i] → shuffledchar[shuffledindices[i]]
- Reverse mapping: shuffledchar[i] → originalchar[position where shuffledindices[position] = i]This creates a bijective (one-to-one) mapping between the original character set and the obfuscated character set, ensuring perfect reversibility.BIP39 Word Cipher (Seed Phrase Mapping)1. Start with the standard BIP39 word list (2048 words)
2. Create an array of indices [0,1,2,...,2047]
3. Apply the seeded Fisher-Yates shuffle to the indices array
4. For each original word at index i, map it to the word at index shuffled_indices[i]
5. Store bidirectional references:
- Original index → Original word
- Original index → Obfuscated index
- Obfuscated index → Obfuscated wordThis creates a comprehensive cipher table that maintains both the word-to-word mapping and the index relationships.Transformation Process### Obfuscation1. For passwords:
- For each character in the original password, look up its corresponding character in the forward mapping and replace it2. For BIP39 seed phrases:
- Split the phrase into individual words
- For each word, find its entry in the cipher table and replace it with the corresponding obfuscated word### Deobfuscation1. For passwords:
- For each character in the obfuscated password, look up its corresponding character in the reverse mapping and replace it2. For BIP39 seed phrases:
- Split the phrase into individual words
- For each word, find its entry in the cipher table (by obfuscated word) and replace it with the corresponding original word## Security Properties### Zero-Trust ArchitectureLifeprints operates with zero trust principles:
- No stored keys or mappings
- No network communication required
- No persistent storage of sensitive data
- Complete client-side operation
- Deterministic output based solely on user inputs### Cryptographic Considerations1. Entropy Source: The security is fundamentally tied to the unpredictability and uniqueness of the user's lifeprint inputs. Personal information known only to the user provides the entropy.2. Brute Force Resistance: The system combines multiple lifeprint inputs, creating a large combinatorial space that makes brute force attacks impractical without knowledge of the user's personal information.3. Reversibility: All transformations are bidirectional by design, allowing for perfect recovery of original data when the same lifeprints are provided.4. Collision Resistance: The 32-bit hash function provides moderate collision resistance. For critical applications requiring higher security, the hash function could be upgraded to a stronger cryptographic hash.5. Forward Secrecy: The system does not provide forward secrecy. If lifeprints are compromised, all historical transformations can be reversed.### Strengths1. Memorability: Utilizes information the user will never forget
2. Offline Operation: Functions completely without internet connectivity
3. No Stored Secrets: Nothing to steal or hack
4. Deterministic: Same inputs always produce same outputs
5. Mental Model Simplicity: Conceptually easier to understand than many cryptographic systems### Limitations1. Shared Knowledge Risk: If lifeprints include information others might know, security is compromised
2. Immutability: Cannot easily change the "key" since it's based on personal history
3. Consistency Requirements: Users must enter lifeprints exactly the same way each time
4. Hash Function Strength: The 32-bit hash provides limited collision resistance## Mathematical IntegrityThe system maintains mathematical integrity through several key properties:1. Bijective Mapping: Every element in the original set maps to exactly one element in the obfuscated set, and vice versa
2. Determinism: The same inputs always produce the same outputs
3. Reproducibility: The transformations can be reproduced independently by anyone with knowledge of the algorithms and the lifeprint inputs
4. Transformation Symmetry: The deobfuscation process is the exact inverse of the obfuscation process## ConclusionLifeprints represents a unique approach to data security that leverages human memory as a key store rather than digital storage. Its mathematical foundations ensure that users can reliably transform sensitive data into obfuscated forms and back again without dependency on external systems or stored mappings.The genius of the system lies in its simplicity and alignment with human cognitive strengths—using information we naturally remember to protect information we shouldn't have to remember.
© Untitled. All rights reserved.
Thank you!
Aliquam sem fringilla ut morbi tincidunt augue interdum velit. Tincidunt tortor aliquam nulla facilisi cras lorem ipsum dolor sit amet.